If online privacy and anonymity are important to you, then you’ve probably heard about Tor (The Onion Router) and VPN (Virtual Private Network).
Tor and VPNs are both internet privacy tools that allow you to bypass censorship, restrictions, and stay anonymous online. They both offer privacy protections for your personal data, but they also differ significantly from one another. This article gives you a detailed rundown of the Tor vs VPN differences.
What is the TOR Browser
Tor is a free and open-source project which lets you surf through the web. But with the extra benefit of anonymity!
So what IS a TOR and does it stand for anything? Well, of course, it does!
The full name of the TOR Browser is “the onion router“. Based on the botanical structures of ONIONS, the TOR Browser makes use of LAYERS which are run by you and me!
If this doesn’t sound brilliant, allow me to explain how TOR Browser works.
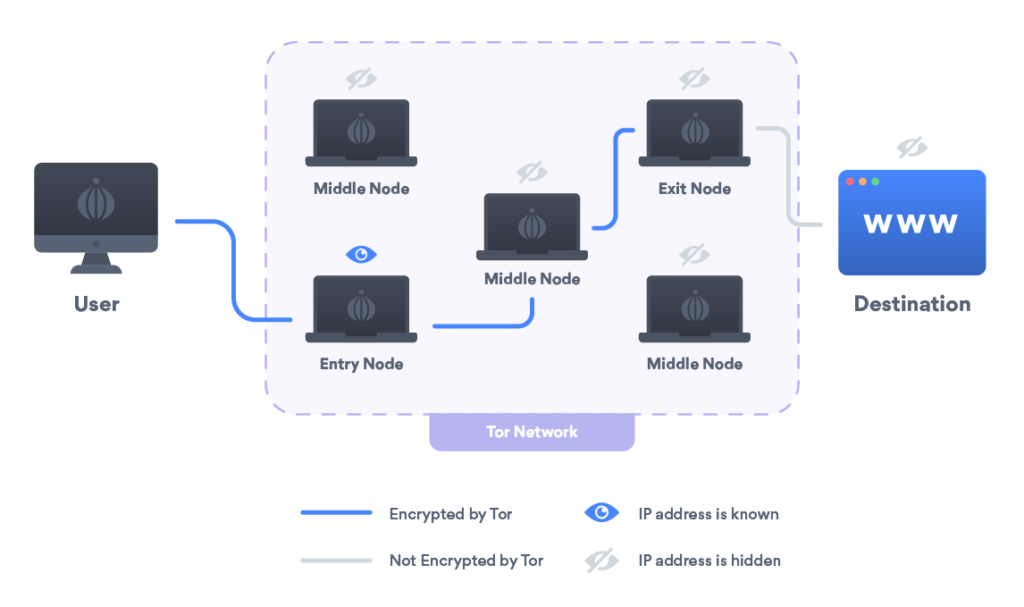
How Does TOR Browser Work?
TOR redirects your connection to a worldwide network of volunteers!
This means your data and mine will be mixed with everyone’s through over 6, 000 volunteers (called relays), making identification DIFFICULT.
This internet encryption process involves relaying your internet traffic, removes non-essential user data, and is of the best privacy tools for any truth-seekers, dark web users, and privacy nuts!
Privacy: Exit Node and Other Encryption Nodes
Just like any relay process, the TOR connections are powered by sending data to the web, which is sent to a randomized node.
The web sends you data back through the exit nodes, and this data (now on your computer) also goes through the encryption and operating systems of TOR.
Internet traffic is sent to the relay connection destination unannounced, and all the exit node knows is where it’s supposed to go.
Who is the data from? The exit node nor the website have ANY idea!
TOR Network: Privacy Secured
Whether you have to perform suspicious work or just someone who loves safety, using TOR keeps your privacy SECURED!
It’s the perfect solution for anyone who wants to make it difficult for anyone to track computer traffic. Using TOR means the user is behind THOUSANDS of other people, without leaving a trace.
It’s no wonder there may be occurrences of slow browsing experience and connection with the TOR network, but hey, we’ll head to that later!
In the meantime, just rave about the data privacy being presented to you by TOR!
What Is a VPN Service
As I would expect most of you to know, a VPN service helps protect your internet freedom, privacy, and freedom of speech by creating connections to networks around the globe!
The simplest way to think about a VPN connection is that VPN servers work as a blanket over your real internet connection.
And it also hides the ENTIRETY of your existence, and not just parts of it! As long as you use a VPN that works exceptionally safe, of course.

How Does VPN Work
Now we can think of VPN as a blanket, but how do these servers work? Well, using a VPN server allows you access to an encryption tunnel that secures your internet traffic and privacy.
When you connect to VPN services, you’re basically establishing a CONNECTION between your device and their server.
Using a VPN as a Middle Man
In this way, you could also think of using a VPN server as utilizing a middleman.
Instead of immediately going to your internet destination, if you use VPN software, it gives you a new IP address at a location available to the VPN providers.
What’s the point of this, you may ask?
By doing this, you’re also able to change your IP address and location!
And even the website will see your connection is from wherever that virtual private network (VPN) server is located, even if you’re not actually there!
And nothing says privacy more than something that’s fake but doesn’t seem fake on the other side of the network traffic.
TOR vs VPN: The Differences
I know I’ve defined both TOR and a VPN, but I understand if it may still be quite difficult to see the differences between them. After all, they ARE quite similar.
But not quite.
You will notice that some of these differences may or may not affect their performance on the dark web, but I’ll let you get into those details later, too!
| Features | TOR | VPN |
|---|---|---|
| Accessibility | High | High |
| Price | Free | Low |
| Speed | Low | High |
| Downloads | None | High |
| Streaming Services | None | Fast |
| Bypassing censorship | Yes | Yes |
| Geo-blocked content access | Depends | Unlimited |
| Anonymity | High | Yes |
TOR vs a VPN: Multitudes and Variety
One of the key differences between TOR and a virtual private network (VPN) is you have a multitude of VPNs available for use. But there is only one TOR network.
This doesn’t really affect its performance, but there might be problems regarding citizens of countries where the use of a VPN might not even be legal!
TOR and VPNs: Their Systems
The other main difference between a TOR vs VPN is their entire SYSTEM; the TOR browser is a decentralized system, while VPN servers are centralized!
Decentralized: TOR Browser
What do I mean by the TOR browser is decentralized? Easy.
This means no one really owns or manages the TOR browser. Its proxy servers, called nodes, are run by thousands of volunteers all over the world, without any ownership staining their names.
Essentially, a TOR browser operates by connecting everyone to a SYSTEM and then having the TOR network randomize the nodes (whether that may be the entrance, middle, or exit nodes).
So when you connect to the TOR browser, there’s the probability that exit nodes could read unencrypted data, but not the source of such data.
Thus, this makes the knowledge of the unencrypted data pretty useless, still leaving you as safe as you were from the very beginning!
But you have to keep in mind that this is ALL voluntary. And this voluntary work in the TOR network is where your internet privacy lies.
Centralized: VPN
Now, what does it mean by a VPN is a centralized service?
Opposite to the TOR network, a VPN is a centralized service.
This means there’s central management in place. Central management has authorization and jurisdiction over the activities of servers, thus requiring the users to have trust in the VPN provider.
No volunteers are present in these systems.
VPN providers could own and operate thousands of servers around the globe, giving their users a wide variety of location options to connect to.
Such a connection then allows you to create an encryption tunnel, providing yourself with privacy in a matter of a few CLICKS!
Basically, VPNs make you look as if you’re somewhere else by changing your IP address, and it’s up to the provider where your privacy lies.
TOR vs VPN: Pros and Cons
Now I’ve discussed the differences, you won’t be confusing these privacy services anymore.
But have you ever wondered at least once throughout the entirety of this article, which one is best for specific users? Which server is best for you and me?
It’s time to find out!
Benefits of TOR Browser
Let’s begin with the benefits of the TOR browser!
Hides Your Online Activities
The most important thing you should know about TOR is its ability to hide your online activities. As I have said multiple times throughout the article, all the data you send through TOR goes through randomized nodes.
Only the last of the sequence is able to see it but without the information of who it was from!
Your browsing and website history, and cookies? They’re all DELETED once you’re done browsing on your computer, too. It simply hides who you are behind all those online activities, without a trace.
In fact, I believe it’s almost impossible to trace someone through the TOR network!
Anti-Spy Internet Connection
Another of the benefits of using TOR is it prevents others from tracking the website you were previously on.
Your data is encrypted ONCE for each of the relays in the TOR network, including the IP address of the next relay.
After which, a layer of encryption is also removed at each relay. BUT it does so while hiding the previous relays from the others.
This means that apart from the fact that TOR is able to hide the existence of your overall activity, it also makes it impossible for anyone to know the websites which were accessed.
After all, those are two different things.
And the TOR server allows you to access BOTH of them!
Anonymity
Anonymity is undoubtedly the main point of the TOR server. To define it and put the TOR network into better perspective, privacy hides what you do. And anonymity hides WHO you are.
Due to the server of TOR being a connection of randomly organized users, it’s able to make all of its users look alike. Almost completely the same, even.
This stops anyone and everyone who attempts to identify you through your browser or your device!
And don’t even get me started about the inability to trace your IP address.
But take note. Nothing on the Internet is ever completely anonymous. The only way to become purely anonymous is to stop using the Internet.
Multi-Layer Encryption
Living to its name, the TOR network is the ultimate representation of an onion network.
Without a doubt, your traffic is encrypted through several LAYERS over and over, and randomly for each of the data you send.
On top of this, it also REDIRECTS your data in several layers!
Your IP address? Before it’s on the second node, it’s encrypted.
But it won’t know who you are; your IP and location were already encrypted before the second node came through!
Anonymity? Why are you even asking, it’s all here in TOR!
Cons of TOR Browser
While all of that does sound good, the use of the TOR network also comes with a few consequences. Shall we begin?
Slow Connection Speed
I’ve mentioned this in the early portions of the article, but if you were also looking for a solution to your slow internet connection, then don’t use TOR. This simply isn’t the network you were looking for.
Your data and website traffic goes through 3 different and randomized relays, and this means your internet can only go as fast as the SLOWEST node.
Literal Internet Traffic: A Case Analysis
Why, you ask? Well, even if you had a pretty quick node, there wouldn’t be a point to it; all of the nodes go in sequence. Let’s say the quick node is at the exit, and your slower node is at the middle.
The data has to get past the middle node, which is going to take some time; and the quick node after it won’t be able to operate until then. A similar scenario occurs if you switch the order.
ONE slow node? This could easily delay the online activity you’re trying to pursue through the network when you use TOR!
DON’T expect a lightning-speed service while you use TOR, for sure.
File Downloads? Next Please
As you now already know, TOR is already slow. It could be even slower than how you imagine it to be. But could you imagine downloading any files on such a network? Even I wouldn’t bother!
In fact, the TOR project has already stated its advice NOT to perform any downloading of sorts when you use TOR.
Vulnerability of the Nodes
One of the things you should know is that not being on an HTTPS connection could actually allow the exit node to see your data.
This ISN’T an issue to the majority of internet users, but it’s still good to know just in case you plan to use TOR!
Accessing Specific Geo-Blocked Content? Good Luck
Due to its randomization, accessing streaming services and other information which are geo-blocked prove to be DIFFICULT. You don’t have ANY control of which country your exit node is going to be in.
Therefore, you also can’t ensure that your IP is going somewhere where the content is available!
Benefits of VPN
Well, I hope you’re through with the pros and cons of using TOR. Let’s move on to the pros and cons of the service under a VPN provider!
Anonymous Website Surfing
This one’s pretty easy, but it’s one of the best packages you’ll get from your VPN provider!
Because VPNs allow you to connect to other tunnels and give you a different IP address, you won’t have a problem trying to hide your identity. In fact, you don’t even have to TRY hiding it.
High-Speed Connection
One of the other things we all should thank our VPN provider is that VPNs still allow you to maintain a good internet connection.
Because you’re still DIRECTLY accessing the content you want, the speed of your WiFi won’t be a problem when you use a VPN!
All you have to know is it’s much, much, faster than going through multiple nodes (like with TOR).
Regional Restrictions? Don’t Matter
Another of the great benefits which come with VPNs is access to content locked by regional restrictions .
When you use a VPN, you’re able to IMMEDIATELY connect to a server where that certain content is allowed.
And what does this mean? Yep, I believe it means you now have a solution to the entire internet freedom problem! And this solution still stands as you fight against those censorship limitations set by the government!
Adaptability
While TOR only runs as a browser, one thing everyone likes about VPNs is its device compatibility!
A VPN secures all of the devices it’s connected to, and it’s even possible to install the VPN to the ROUTER itself!
Cons of VPN
Just like TOR, the benefits of VPNs have their consequences, too!
Paid Services
As one can imagine, changing your IP addresses safely could be potentially expensive. And our anonymity is the price VPNs pay us in exchange.
Of course, there are FREE VPNs like Speedify. But how sure of their safety are you? I know they could be dangerous, so I advise you to stray away.
What do you suppose could happen if the information gets into the wrong hands? Neither of us will really know.
No Logs Policies
One of the things you have to ensure with VPNs is they should have a no-logs policy. And they should live by it.
Without the no-logs policy, your data could be in immediate DANGER. Choose your VPN carefully and WISELY!
A Single System
This isn’t really much of an issue when it comes to a secure VPN, but I can’t deny how a VPN might be much easier to track compared to the layered system of TOR.
As long as you use a VPN that’s safe and devotes itself to privacy, I’m sure you’ll be fine, though!
FAQs
Is TOR better than VPN?
Whichever is better between TOR and VPNs wholly depends on your online activity.
If you have to secure the information you’re viewing at all costs (like the dark web), then the battle between TOR and VPNs would lean towards TOR!
Otherwise, you’d do better with a VPN since it’s secure yet doesn’t compromise speed.
Is TOR secure without a VPN?
Yes, TOR is secure even without a VPN! It does use a multi-layered system, after all.
What’s the Difference: TOR vs VPN?
The difference between TOR and VPNs lies mostly in the type of system they are. A TOR is completely voluntary and isn’t managed by a single management.
In turn, this is also where its layers are born from.
On the other hand, a VPN is led by a single provider and operates on a linear system with a multitude of IP options.
Are TOR and VPN Illegal?
Both TOR and VPN are illegal or restricted in SOME areas. However, the majority of the tech players, including me, advise against the use of TOR.
The use of VPN is predominantly legal around the world, though!
Is VPN Dangerous?
Using a FREE VPN may pose a threat to the privacy of your data. When you use a VPN, you prevent your data from being monitored by your ISP, but you’re trusting the VPN provider with some of your traffic.
On this note, I advise avoiding using a free VPN, and always make sure the VPN you’re using has a strong commitment to its no-logs policies.
Should I Use VPN, TOR, at the Same Time?
You could use both VPN, TOR at the same time, but it’s not necessary. Unless you’re really committed to accessing information that requires you to use TOR even more securely.
Using both TOR and a VPN is definitely possible, though!
Conclusion
There are definitely a few differences between TOR and VPN which we all have to take note of to ensure our online protection.
Whichever of the two you use, all I hope is you get both the PRIVACY and ANONYMITY you deserve!
