Advanced Encryption Standard (formerly known as Rijndael) is one of the ways of encrypting information. It’s so secure that even brute force couldn’t possibly break it. This advanced encryption standard is used by the National Security Agency (NSA) along with multiple industries, including online banking. So, what is AES Encryption and how does it work? Let’s find out!
Short summary: What is AES-256 Encryption? AES-256 encryption is a way of keeping secret messages or information safe from people who shouldn’t be able to see it. AES-256 encryption is like having a super strong lock on your box that can only be opened by a very specific key. The lock is so strong that it would be very difficult for someone to break it and open the box without the right key.
What Is AES Encryption?
AES is the data encryption standard of today. It’s unparalleled in the amount of security and protection it offers.
Let’s break down what it is. AES is a
- Symmetric key encryption
- Block cipher
Symmetric vs. Asymmetric Encryption
AES is a symmetric type of encryption.
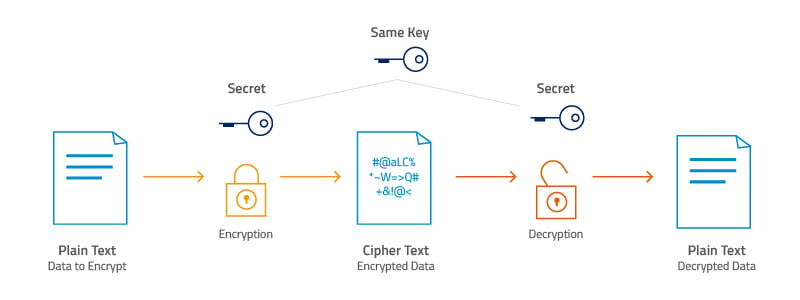
“Symmetric” means it uses the same key to both encrypt and decrypts information Moreover, both the sender and receiver of the data need a copy of it to decrypt the cipher.
On the other hand, asymmetric key systems use a different key for each of the two processes: encryption and decryption.
The advantage of symmetric systems like AES is they’re much faster than asymmetric ones. This is because symmetric key algorithms require less computing power.
This is why asymmetric keys are best used for external file transfers. Symmetric keys are better for internal encryption.
What Are Block Ciphers?
Next, AES is also what the tech world calls a “block cipher.”
It’s called “block” because this type of cipher divides the information to be encrypted (known as plaintext) into sections called blocks.
To be more specific, AES uses a 128-bit block size.
This means the data is divided into a four-by-four array containing 16 bytes. Each byte contains eight bits.
Hence, 16 bytes multiplied by 8 bits is yields a total of 128 bits in each block.
Regardless of this division, the size of the encrypted data remains the same. In other words, 128 bits of plaintext yields 128 bits of ciphertext.
The Secret to the AES Algorithm
Now hold on to your hats because here’s where it gets interesting.
Joan Daemen and Vincent Rijmen made the brilliant decision of using the Substitution Permutation Network (SPN) algorithm.
SPN works by applying multiple rounds of key expansion to encrypt data.
The initial key is used to create a series of new keys called “round keys.”
We’ll get more into how these round keys are generated later. Suffice to say that, multiple rounds of modification generate a new round key every time.
With each passing round, the data becomes more and more secure and it becomes harder to break the encryption.
Why?
Because these encryption rounds make AES impenetrable! There are just way too many rounds that hackers need to break through to decrypt it.
Put it this way: A supercomputer would take more years than the presumed age of the universe to crack an AES code.
To this date, AES is practically threat-free.
The Different Key Lengths
There are three lengths of AES encryption keys.
Each key length has a different number of possible key combinations:
- 128-bit key length: 3.4 x 1038
- 192-bit key length: 6.2 x 1057
- 256-bit key length: 1.1 x 1077
While the key length of this encryption method varies, its block size – 128-bits (or 16 bytes) – remains the same.
Why the difference in key size? It’s all about practicality.
Let’s take an app for example. If it uses 256-bit AES instead of AES 128, it will require more computing power.
The practical effect is it will require more raw power from your battery, so your phone will die faster.
So while using AES 256-bit encryption is the gold standard, it’s just not feasible for everyday use.
Where Is Advanced Encryption Standard (AES) Used?
AES is one of the most trusted systems in the world. It’s been widely adopted in multiple industries that need extremely high levels of security.
Today, AES libraries have been created for numerous programming languages including C, C++, Java, Javascript, and Python.
The AES encryption standard is also used by different file compression programs including 7 Zip, WinZip, and RAR, and disk encryption systems like BitLocker and FileVault; and file systems like NTFS.
You may have already been using it in your daily life without you noticing!
AES is a vital tool in database encryption and VPN systems.
If you rely on password managers to remember your login credentials for your multiple accounts, likely, you’ve already encountered AES!
Those messaging apps that you use, like WhatsApp and Facebook Messenger? Yeah, they use this, too.
Even video games like Grand Theft Auto IV use AES to guard against hackers.
An AES instruction set is integrated into all Intel and AMD processors, so your PC or laptop already has it built-in without you having to do anything.
And of course, let’s not forget the apps your bank created to let you manage your finances online.
After you find out how AES encryption works, you’ll breathe much easier with the knowledge that your information is in safe hands!
History of AES Encryption
AES started as a response U.S. government’s needs.
Back in 1977, federal agencies would rely on the Data Encryption Standard (DES) as their primary encryption algorithm.
However, by the 1990s, DES was no longer secure enough because it could be broken in only 22 hours.
So, the government announced a public competition to find a new system that lasted over 5 years.
The benefit of this open process was that each of the submitted encryption algorithms could be subjected to public security. This meant the government could be 100% certain that their winning system had no backdoor.
Moreover, because multiple minds and eyes were involved, the government maximized its chances of identifying and fixing flaws.
FINALLY, the Rijndael cipher (aka today’s Advanced Encryption Standard) was crowned the champion.
Rijndael was named after the two Belgian cryptographers who created it, Vincent Rijmen and Joan Daemen.
In 2002, it was renamed the Advanced Encryption Standard and published by the U.S. National Institute of Standards and Technology (NIST).
The NSA approved the AES algorithm for its ability and security to handle top-secret information. THIS put AES on the map.
Since then, AES has become the industry standard for encryption.
Its open nature means the AES software can be used for both public and private, commercial and noncommercial applications.
How Does AES 256 Work?
Encryption and decryption are the fundamental building blocks of modern data security.
Encryption involves transforming plaintext into ciphertext, while decryption is the reverse process of transforming ciphertext back into plaintext.
To achieve this, encryption algorithms use a combination of processing steps, including substitution and permutation operations, which operate on a state array.
The state array is modified by a series of round versions, with the number of rounds determined by the encryption key size and the algorithm’s bit block size.
The encryption key and the decryption key are required to transform the data, with the encryption key used to generate the ciphertext and the decryption key used to generate the original plaintext.
The advanced encryption standard (AES) uses an expansion process to generate a key schedule, and a network structure that includes byte substitution and permutation operations to achieve data protection.
So far, we know that these encryption algorithms scramble the information it’s protecting and turn it into a random mess.
I mean, the basic principle of all encryption is each unit of data will be replaced by a different one, depending on the security key.
But what exactly makes AES encryption secure enough to be considered the industry standard?
An Overview of the Process
In today’s digital age, internet security and data security have become a top priority for both individuals and organizations.
Governments around the world also place a strong emphasis on protecting their sensitive information and use various security measures to do so.
One such measure is the use of advanced encryption techniques to safeguard user data.
Encryption helps to protect data at rest and in transit by converting it into unreadable cipher text that can only be decrypted with a key.
By using encryption to protect data, governments and other organizations can ensure that sensitive information remains secure and confidential, even if it falls into the wrong hands.
The strength of encryption depends on various factors such as the length of the cipher key, the number of rounds, and the cipher security.
Whether it is byte data or bit data, encryption plays a crucial role in maintaining data security and confidentiality.
The AES encryption algorithm goes through multiple rounds of encryption. It can even go through 9, 11, or 13 rounds of this.
Each round involves the same steps below.
- Divide the data into blocks.
- Key expansion.
- Add the round key.
- Substitute/replacement of the bytes.
- Shift the rows.
- Mix the columns.
- Add a round key again.
- Do it all over again.
After the last round, the algorithm will go through one additional round. In this set, the algorithm will do steps 1 to 7 except step 6.
It alters the 6th step because it would not do much at this point. Remember it’s already gone through this process multiple times.
So, a repeat of step 6 would be redundant. The amount of processing power it would take to mix the columns again just isn’t worth it as it will no longer significantly alter the data.
At this point, the data will have already gone through the following rounds:
- 128-bit key: 10 rounds
- 192-bit key: 12 rounds
- 256-bit key: 14 rounds
The output?
A random set of jumbled characters that won’t make sense to anyone who doesn’t have the AES key.
An In-Depth Look
You now have an idea of how this symmetric block cipher is made. Let’s go into more detail.
First, these encryption algorithms add the initial key to the block using an XOR (“exclusive or”) cipher.
This cipher is an operation built into processor hardware.
Then, each byte of data is substituted with another.
This CRUCIAL step will follow a predetermined table called Rijndael’s key schedule to determine how each replacement is made.
Now, you’ve got a set of new 128-bit round keys that are already a mess of jumbled letters.
Third, it’s time to go through the first round of AES encryption. The algorithm will add the initial key to the new round keys.
Now you’ve got your second random cipher.
Fourth, the algorithm substitutes every byte with a code according to the Rijndael S-box.
Now, it’s time to shift the rows of the 4×4 array.
- The first row stays where it is.
- The second row gets moved one space to the left.
- The third row is shifted into two spaces.
- Finally, the fourth is moved three spaces.
Sixth, each column will be multiplied by a predefined matrix which will again give you a new block of code.
We won’t go into detail because this is an extremely complicated process that requires tons of advanced math.
Just know the columns of the cipher are mixed and combined to come up with another block.
Finally, it will add the round key to the block (much like the initial key was in the third step).
Then, rinse and repeat based on the number of rounds you need to do.
The process continues several more times, giving you ciphertext that’s radically different from the plaintext.
To decrypt it, do the whole thing in reverse!
Each stage of the AES encryption algorithm serves an important function.
Why All the Steps?
Using a different key for each round gives you a much more complex result, keeping your data safe from any brute-force attack regardless of the key size you’re using.
The byte substitution process modifies the data in a nonlinear way. This hides the relationship between the original and encrypted content.
Shifting the rows and mixing the columns will diffuse the data. Shifting diffuses the data horizontally, while mixing does so vertically.
By transposing bytes, you’ll get much more complicated encryption.
The result is an incredibly sophisticated form of encryption that can’t be hacked unless you have the secret key.
Is AES Encryption Secure?
If our description of the process isn’t enough to make you believe in the power of the AES key, let’s dive into how secure AES is.
Like we said in the beginning, the National Institute of Standards and Technology (NIST) selected three kinds of AES: 128-bit AES, 192-bit, and 256-bit keys.
Each type still uses the same 128-bit blocks, but they differ in 2 things.
Key Length
The first difference lies in the length of each of the bit keys.
As the longest, AES 256-bit encryption provides the strongest level of encryption.
This is because a 256-bit AES encryption would require a hacker to try 2256 different combinations to ensure the right one is included.
We need to emphasize this number is astronomically large. It’s a total of 78 digits!
If you still don’t understand how big it is, let’s put it this way. It’s so big that it’s exponentially greater than the number of atoms in the observable universe.
Obviously, in the interest of protecting national security and other data, the U.S. government requires a 128- or 256-bit encryption process for sensitive data.
AES-256, which has a key length of 256 bits, supports the largest bit size and is practically unbreakable by brute force based on current computing power standards, making it, as of today, the strongest encryption standard there is.
| Key Size | Possible Combinations |
| 1 bit | 2 |
| 2 bits | 4 |
| 4 bits | 16 |
| 8 bits | 256 |
| 16 bits | 65536 |
| 32 bits | 4.2 x 109 |
| 56 bits (DES) | 7.2 x 1016 |
| 64 bits | 1.8 x 1019 |
| 128 bits (AES) | 3.4 x 1038 |
| 192 bits (AES) | 6.2 x 1057 |
| 256 bits (AES) | 1.1 x 1077 |
Encryption Rounds
The second difference between these three AES varieties is in the number of rounds of encryption it goes through.
128-bit AES encryption uses 10 rounds, AES 192 uses 12 rounds, and AES 256 uses 14 rounds.
As you’ve probably guessed, the more rounds you use, the more complex the encryption becomes. This is mainly what makes AES 256 the most secure AES implementation.
The Catch
A longer key and more rounds will require higher performance and more resources/power.
AES 256 uses 40% more system resources than AES 192.
This is why the 256-bit Advanced Encryption standard is best for high-sensitivity environments, like the government when it deals with sensitive data.
These are the cases where security is more important than speed or power.
Can Hackers Crack AES 256?
The old 56-bit DES key could be cracked in less than a day. But for AES? It would take billions of years to break using the computing technology we have today.
Hackers would be foolish to even attempt this type of attack.
That being said, we have to admit no encryption system is entirely secure.
Researchers who have looked into AES have found a few potential ways to get in.
Threat #1: Related-Key Attacks
In 2009, they discovered a possible related-key attack. Instead of brute force, these attacks will target the encryption key itself.
This type of cryptanalysis will attempt to crack a cipher by observing how it operates using different keys.
Fortunately, the related-key attack is only a threat to AES systems. The only way it can work is if the hacker knows (or suspects) the relationship between two sets of keys.
Rest assured, cryptographers were quick to improve the complexity of the AES key schedule after these attacks to prevent them.
Threat #2: Known-Key Distinguishing Attack
Unlike brute force, this attack used a known key to decipher the structure of the encryption.
However, the hack only targeted an eight-round version of AES 128, not the standard 10-round version. However, this isn’t a major threat.
Threat #3: Side-Channel Attacks
This is the main risk AES faces. It works by trying to pick up any information the system is leaking.
Hackers can listen to sounds, electromagnetic signals, timing information, or power consumption to try and figure out how the security algorithms work.
The best way to prevent side-channel attacks is by removing information leaks or masking the leaked data (by generating extra electromagnetic signals or sounds).
Threat #4: Revealing the Key
This is easy enough to prove by doing the following:
- Strong passwords
- Multifactor authentication
- Firewalls
- Antivirus software
Moreover, educate your employees against social engineering and phishing attacks.
The Advantages of AES Encryption
When it comes to encryption, key management is crucial. AES, for instance, uses different key sizes, with the most commonly used being 128, 192, and 256 bits.
The key selection process involves generating a secure key based on a set of rules, such as randomness and unpredictability.
Additionally, encryption keys, also known as cipher keys, are used to encrypt and decrypt data. The advanced encryption process also includes a round key, which is generated from the original key during the encryption process.
However, a key recovery attack or a side channel attack can compromise the security of the encryption system.
This is why security systems often use military-grade encryption and multi-factor authentication to ensure the highest level of protection.
The encryption process of AES is relatively easy to understand. This allows for easy implementation, as well as really fast encryption and decryption times.
Moreover, AES requires less memory than other types of encryption (like DES).
Finally, whenever you require an extra layer of safety, you can easily combine AES with various security protocols like WPA2 or even other types of encryption like SSL.
AES vs ChaCha20
AES has some limitations that other types of encryption have tried to fill.
While AES is fantastic for most modern computers, it’s not built into our phones or tablets.
This is why AES is typically implemented through software (instead of hardware) on mobile devices.
However, the software implementation of AES takes up too much battery life.
ChaCha20 also uses 256-bit keys. It was developed by several engineers from Google to fill this gap.
Advantages of ChaCha20:
- More CPU friendly
- Easier to implement
- Requires less power
- More secure against cache-timing attacks
- It’s also a 256-bit key
AES vs Twofish
Twofish was one of the finalists in the competition the government held to replace DEs.
Instead of the blocks, Twofish uses a Feistel network. This means it’s a similar but more complex version of older standards like DES.
Until today, Twofish remains unbroken. This is why many say it’s safer than AES, considering the potential threats we mentioned earlier.
The main difference is that AES varies the number of rounds of encryption depending on the key length, while Twofish keeps it at a constant of 16 rounds.
However, Twofish requires more memory and power compared to AES, which is its biggest downfall when it comes to using mobile or lower-end computing devices.
Conclusion
If AES 256 bit encryption is good enough for the National Security Agency, we’re more than willing to trust in its security.
Despite the many technologies available today, AES remains at the top of the pack. It’s good enough for any company to use for their top-secret information.
References
- https://www.atpinc.com/blog/what-is-aes-256-encryption
- https://www.samiam.org/key-schedule.html
- https://www.youtube.com/watch?v=vFXgbEL7DhI
- https://digitalguardian.com/blog/social-engineering-attacks-common-techniques-how-prevent-attack
- https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams
